In the fight against spam, spam filters are the front line of defense, protecting us from unwanted and potentially harmful email.
But what exactly are spam filters and how do they work?
In this article, we will delve into the realm of spam filtering, exploring its basic concepts, mechanisms, and classifications. From understanding the nature of spam filtering to dissecting the intricate workings of these digital gatekeepers, we will attempt to bring clarity to a topic that affects virtually every email user.
So read on, and let’s dive in and unravel the mysteries of spam filters together.
TABLE OF CONTENTS
– What is spam filtering?
– How does a spam filter work?
– Categories of email spam filters
– Types of spam filters
– Tips to avoid spam filters
What is spam filtering?
Spam filtering is the process of identifying and categorizing unsolicited or unwanted email, known as spam, and preventing it from reaching a recipient’s inbox.
It serves as a critical defense mechanism against the ever-increasing volume of spam that is flooding email servers and inboxes worldwide.
Using a variety of algorithms and techniques, spam filters analyze incoming email, assessing its content, sender reputation, and other factors to determine whether it is legitimate or unwanted.
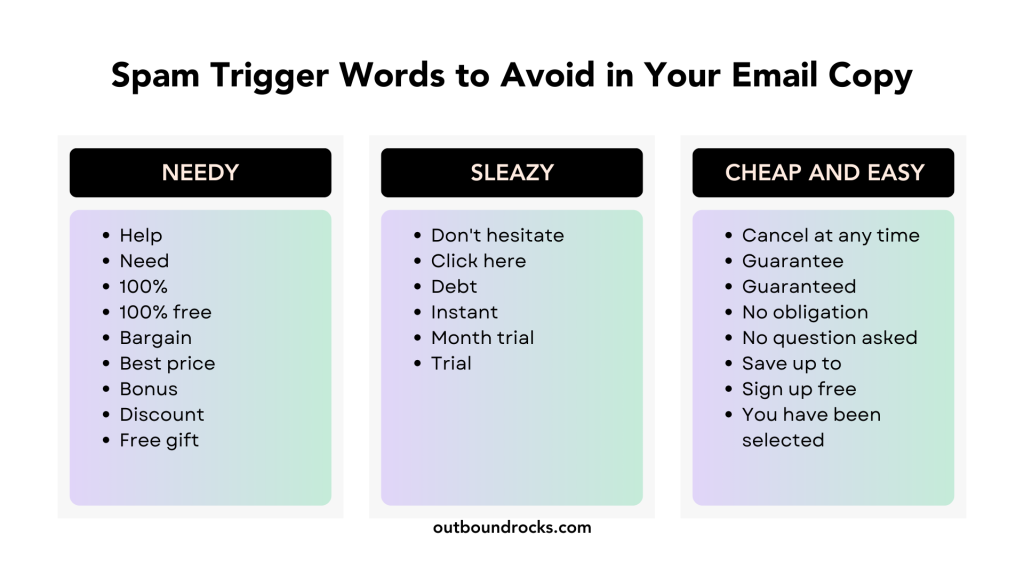
Want to learn more? This is a powerful list of 70 spam trigger words to avoid in 2024. Pleae, click the image below to read the article:

How does a spam filter work?
In technical terms, an email spam filter is a software application that examines incoming email for signs of unwanted, harmful, or malicious content.
It uses various algorithms and criteria to identify spam, malware, or phishing attempts, and then isolates such emails by either quarantining them, rejecting them outright, or redirecting them to a designated junk folder.
By using spam filters, users can protect themselves from a range of potential threats, including:
- Preventing the theft of personal or customer information through malicious email.
- Reduce the risk of their devices being hijacked by bad actors and used as spam bots.
- Maintain a clutter-free inbox by filtering out unwanted messages so users can focus on important communications.
- Protect against cyberattacks launched through deceptive email tactics.
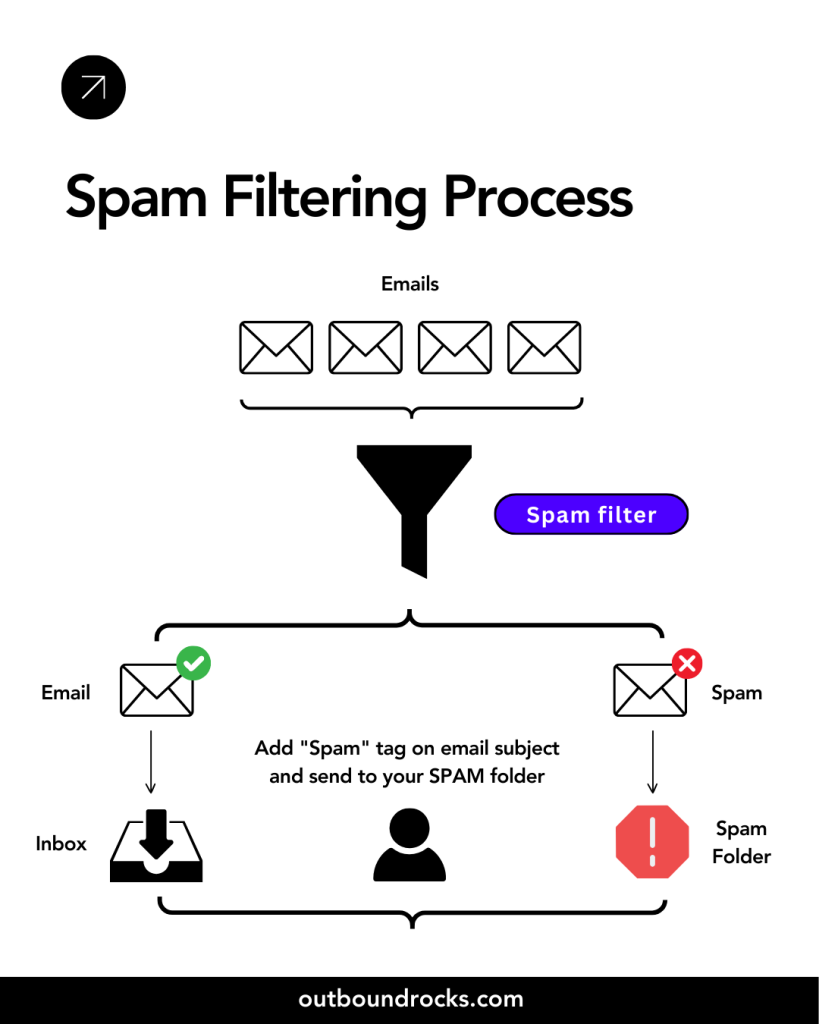
Categories of email spam filters
Based on where they reside in the email process, email spam filters can be divided into three broad categories:
| Categories | Description |
| Gateway | Is typically physical hardware that resides behind a network’s firewall on an on-premises server, not in the cloud. It acts as a security gate on the network, preventing malicious and spam email from entering the email server. |
| Hosted | Unlike the gateway email spam filter, this one resides in the cloud. This email anti-spam filter works similarly to the gateway anti-spam filter, preventing spam email from entering the system network. |
| Desktop | These are installed locally on the computer, usually by the user, and allow for easy configuration and customization. |
Types of spam filters
There are several types of e-mail spam filters, each of which uses different techniques to identify and block unwanted e-mail. Here are five of the more common types:
1. Content filters
Content filters analyze the content of emails, including text, images, links, and attachments, to identify patterns commonly associated with spam.
They look for specific keywords, phrases, or characteristics that indicate the email is unwanted or potentially harmful. Content filters can also evaluate the formatting, structure, and overall quality of the email content to determine its legitimacy.
2. Blacklist filters
Blacklist filters maintain lists of known spam sources, such as IP addresses, domains, or email addresses that have been reported for sending unwanted or malicious email.
When email arrives from a blacklisted source, it is automatically flagged as spam and either quarantined or rejected outright. Blacklist filtering helps prevent repeat offenders from reaching users’ inboxes.
3. Header filters
These filters examine the metadata of an email, including information such as the sender address, subject line, and routing information.
By analyzing the header of an email, these filters can detect signs of spoofing or forging, common tactics used by spammers to disguise their true identity or evade traditional spam detection methods.
4. Language filters
Language and country filters analyze the language used in an email and the geographic origin of the sender to determine its legitimacy. For example, if an email is written in a language or originates from a country known for spamming activity, it may be flagged as suspicious and subjected to additional scrutiny.
These filters help protect against spam campaigns that target specific regions or language-speaking populations.
5. Rule-Based filters
Rule-based filters operate according to a set of predefined rules or criteria set by the email administrator or security team. These rules can be based on a variety of factors, such as keywords, sender reputation, email format, or attachment types.
If an incoming email matches one or more of these rules, it is flagged as spam and subjected to further review or action, such as quarantine or rejection.
Tips to avoid spam filters
As spam filters become more sophisticated, it’s important to adopt proactive strategies to avoid being flagged as spam.
Here are some valuable tips to help you navigate the ever-evolving landscape of email filtering and maintain a strong sender reputation:
- Maintain an impeccable sender reputation
- Optimize email content and subject lines, maintain a good image-to-text ratio, and avoid excessive links;
- Obtain permission from recipients before sending emails;
- Maintain high engagement rates.
Conclusions
Are you ready to take your email marketing to the next level? Try our free demo today and discover how Outbound Rocks can help you optimize your sales funnel and connect with your ideal prospects.